- 1-888-479-0741
- sales@dotcom-monitor.com
- Minneapolis, MN, USA
Enhance Security with Industry Standards Protocols
![]() Simplify access and boost security with SSO
Simplify access and boost security with SSO
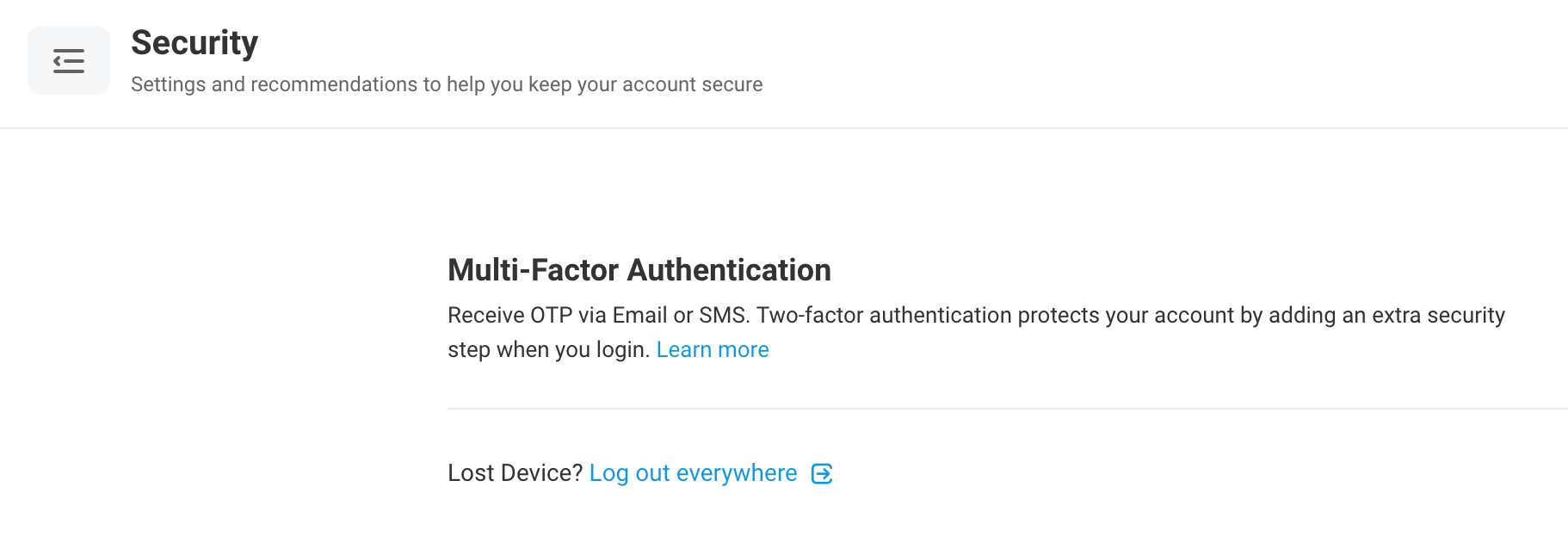
![]() Strengthen account security with increased verification
Strengthen account security with increased verification
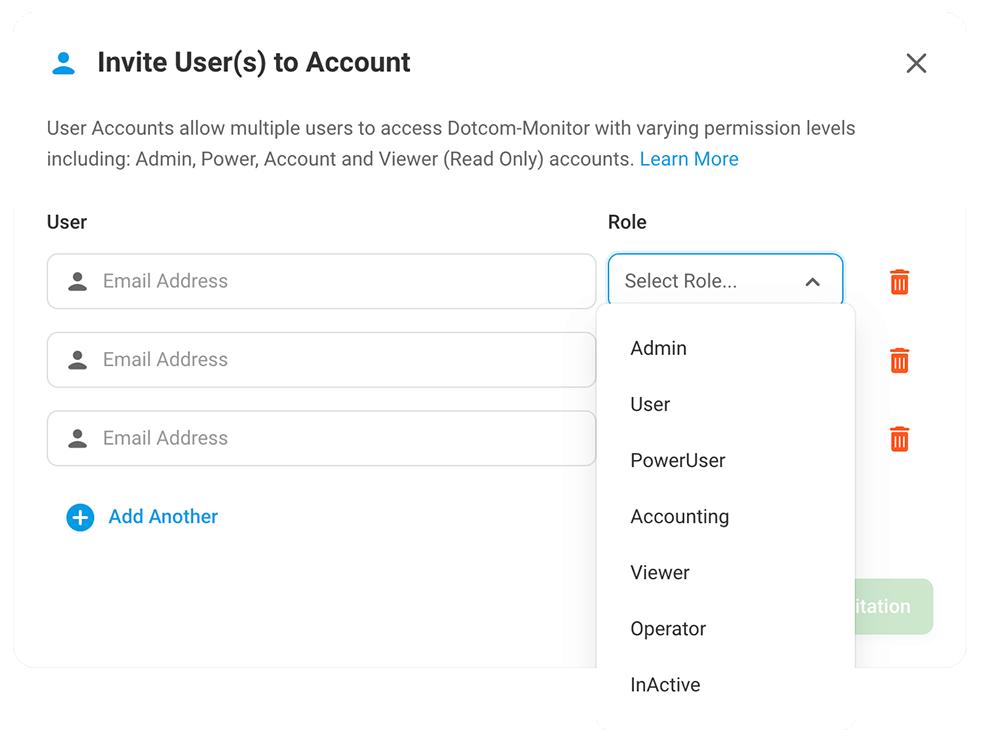
![]() Define user access via user groups and departments
Define user access via user groups and departments
Advanced Protocols
Safeguarding Your Digital Systems
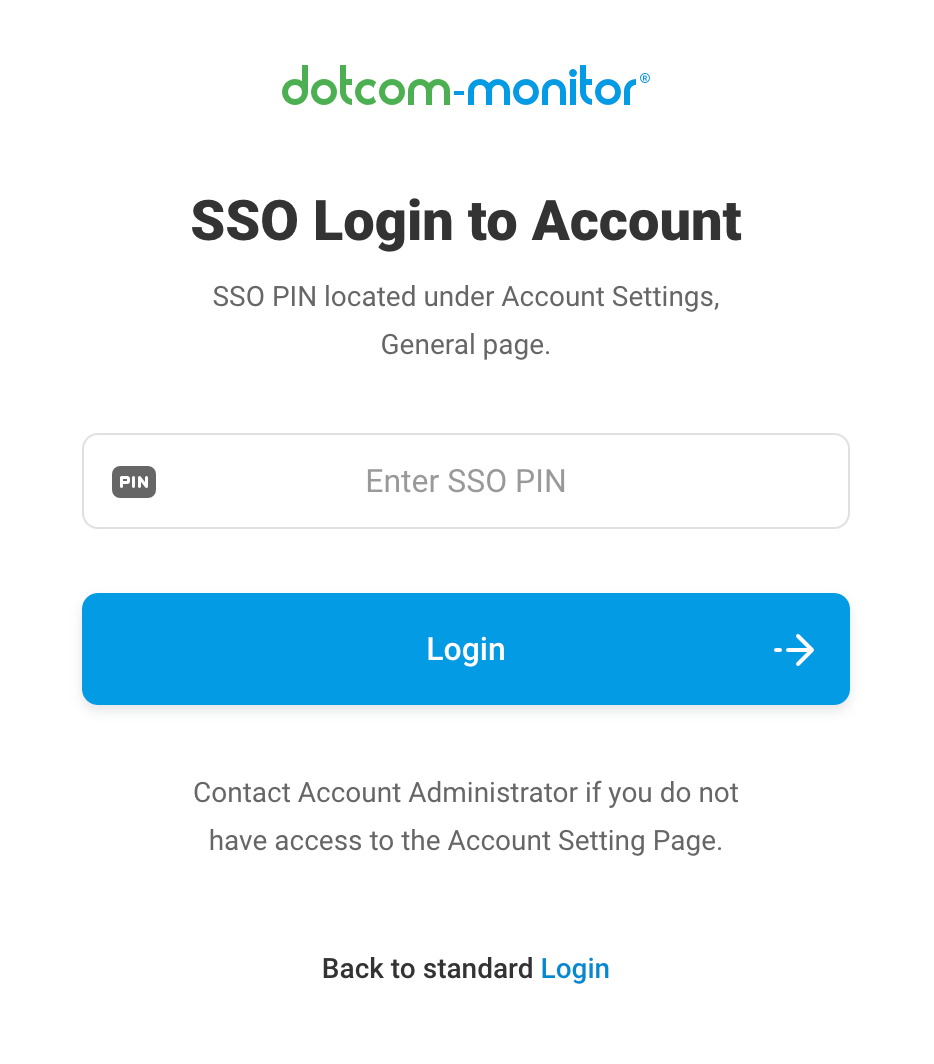
Unified Access for Dotcom-Monitor with Single Sign-On
Boost your security and streamline access with Dotcom-Monitor's Single Sign-On (SSO). SSO lets users log in once for all monitoring tools by simplifying credentials and centralizing authentication. Easily integrate with your identity management systems for quick, secure access to Dotcom-Monitor.
Extra Layer of Protection with Multi-Factor Authentication
Secure your account with Multi-Factor Authentication (MFA) which requires multiple verification factors for enhanced protection. Avoid unauthorized access and any compromises by easily integrating MFA with your existing security protocols for added safety and peace of mind.
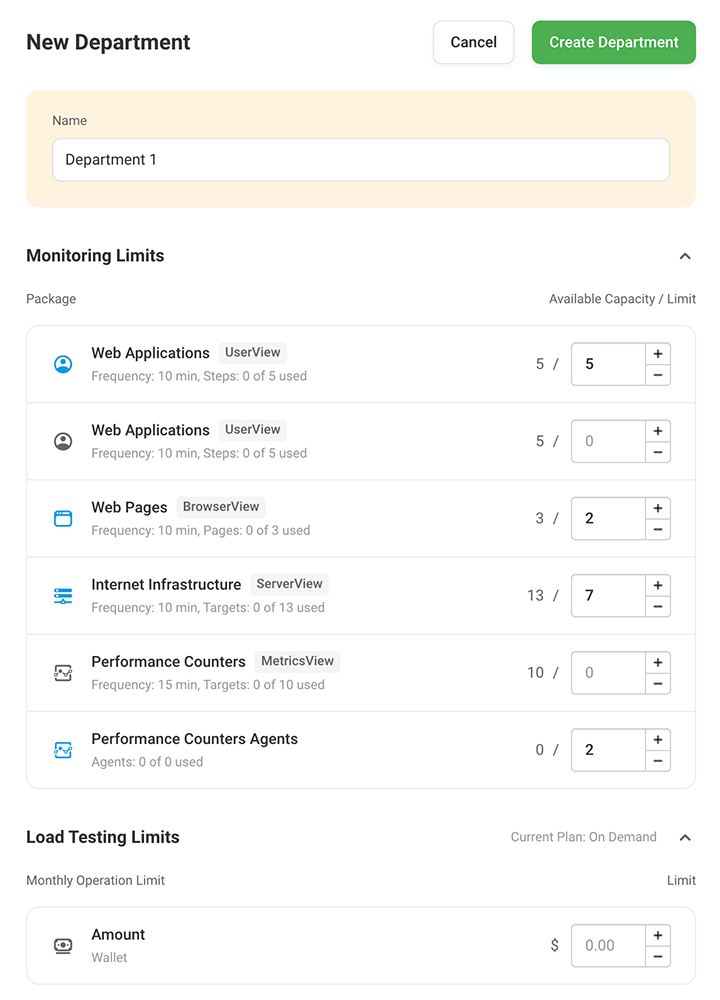
Streamlined Management with Master and Sub-Accounts
Dotcom-Monitor structures its service with a master account that includes various departments and sub-accounts. This promotes efficient management of large groups and diverse user types, which allows each department to address specific monitoring and resource needs through its sub-accounts.
USER ROLES
Define Your Users
Ensuring secure and reliable access to your data is a top priority for Dotcom-Monitor. Assign roles to different users based on their access needs and use additional tools to manage multi-user access. The Dotcom-Monitor system also creates audit trails for all user interactions which enables you to monitor activity and track any changes made.

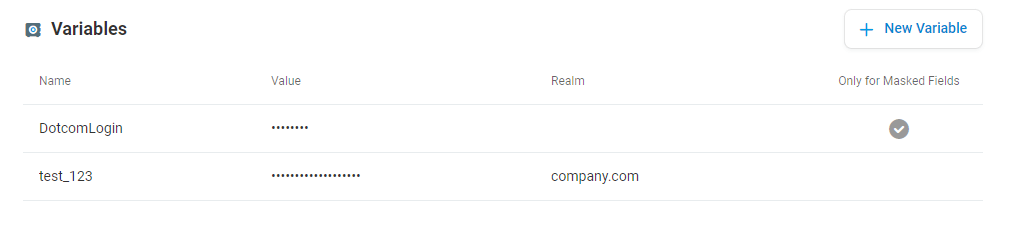
Secure Sensitive Data
Take advantage of Secure Vault as it offers encrypted containers, known as Crypts, to store sensitive data. Data marked as Crypt Variables are encrypted and can be used in testing web services, internet infrastructure, and EveryStep scripts. Access to view and modify this encrypted data is restricted to users with the necessary permissions.


